Data Security
Data Security
The threat to data has never been greater. Oracle Database helps reduce the risk of a data breach and simplifies regulatory compliance with security solutions for encryption and key management, granular access controls, flexible data masking, comprehensive activity monitoring, and sophisticated auditing capabilities.
Content Detail
Dropdown link
Oracle Database Security
Oracle Database Security
Product Description
Data is one of the most important assets for any organization. As such, it is paramount to safeguard data from any and all unauthorized access. Data breaches, failed audits, and failure to comply with regulatory requirements can all result in reputational damage, loss of brand equity, compromised intellectual property, and fines for noncompliance. Under the European Union General Data Protection Regulation (GDPR), data breaches can lead to fines of up to 4% of an organization’s global annual revenue, often resulting in significant financial loss. Sensitive data includes personally identifiable information, financial information, health information, and intellectual property. Data must be protected to help avoid a data breach and to help achieve compliance.
Product IMAGE
Product FEAtures
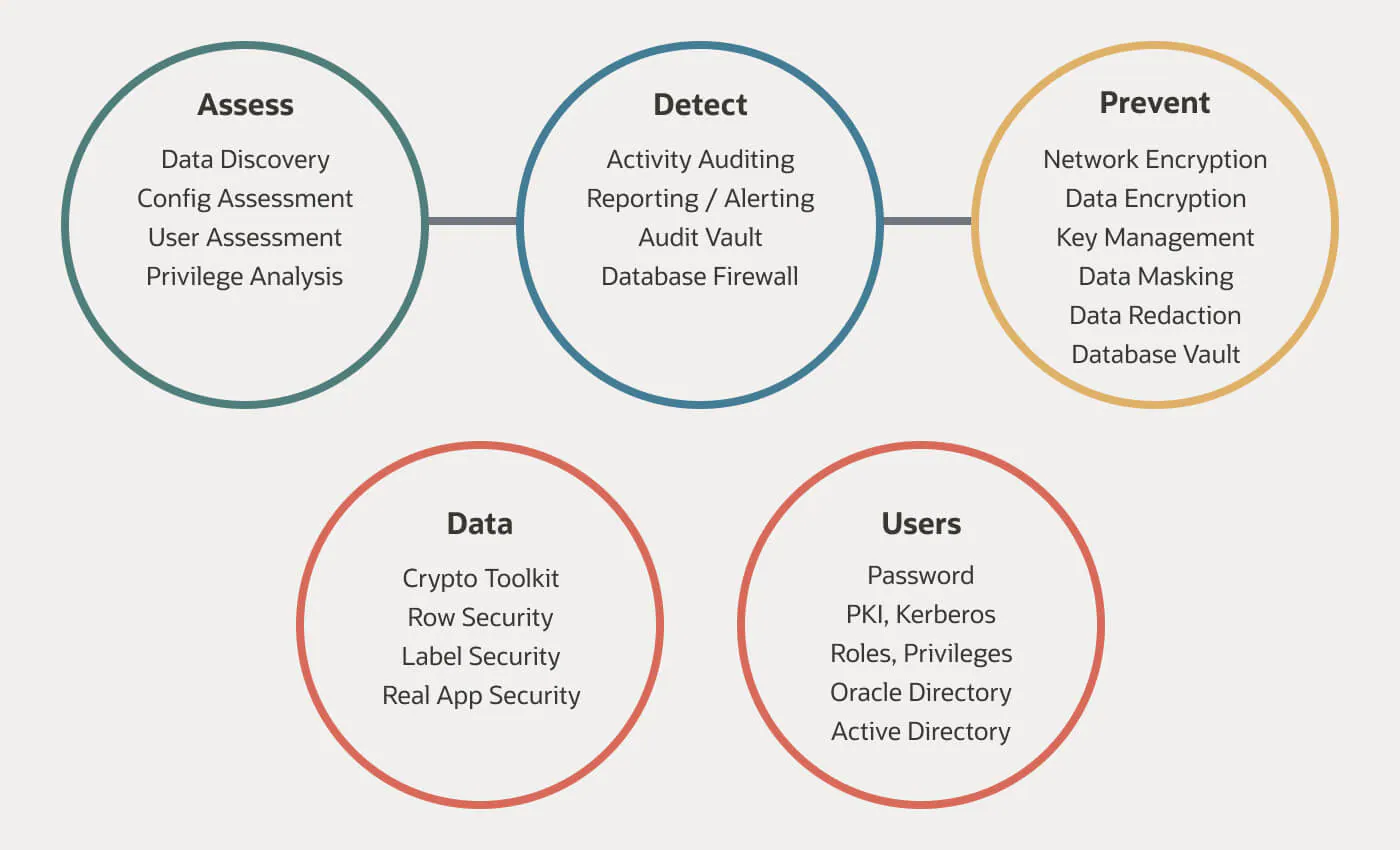
A well-structured database security strategy should include controls to mitigate a variety of threat vectors. The best approach is a built-in framework of security controls that can be deployed easily to apply appropriate levels of security. Here are some of the more commonly used controls for securing databases:
- Assessment controls help to assess the security posture of a database and should also offer the ability to identify configuration changes. Organizations can set a baseline and then identify drift. Assessment controls also help organizations to identify sensitive data in the system, including type of data and where it resides. Assessment controls seek to answer the following questions:
- Is the database system configured properly?
- Are patches up-to-date and applied regularly?
- How are user privileges managed?
- What sensitive data is in the database system? How much? Where does it reside?
- Detective controls monitor user and application access to data, identify anomalous behaviors, detect and block threats, and audit database activity to deliver compliance reporting.
- Preventive controls block unauthorized access to data by encrypting, redacting, masking, and subsetting data, based on the intended use case. The end goal of preventive controls is to halt unauthorized access to data.
- Data-specific controls enforce application-level access policies within the database, providing a consistent authorization model across multiple applications, reporting tools, and database clients.
- User-specific controls enforce proper user authentication and authorization policies, ensuring that only authenticated and authorized users have access to data.
Link Document

